Implementation
Get started with data privacy protection easily and quickly

The Privinity Privacy Platform is designed for rapid implementation with minimal IT dependencies and management. This allows you to get started with implementing your data privacy protection measures faster than ever before!
Key advantages
How it works
1.
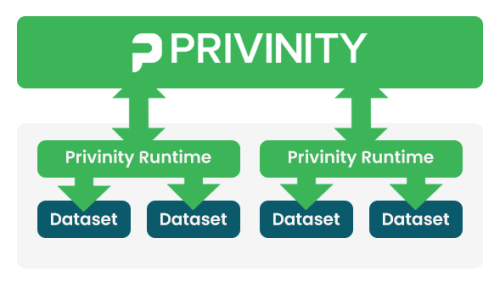
Connect your on-premises infrastructure to your Privinity Privacy Platform environment
Bridge the gap between your on-premises data sources and the Privinity Privacy Platform using the Privinity Runtime client. The Privinity Runtime client ensures the secure anonymization of your data within your own on-premises infrastructure, while control and monitoring are centralized within your own Privinity Privacy Platform environment.
2.
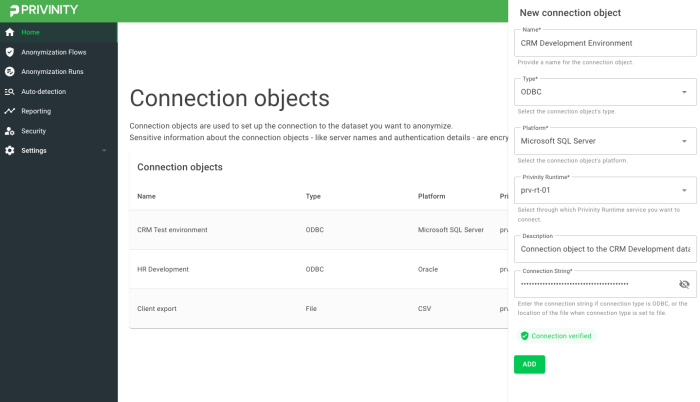
Connect to the data sources you want to protect
Through the Privinity Runtime client, you can connect to various types of datasets, ranging from individual files in CSV format to complete databases such as Oracle, Microsoft SQL Server, and MySQL.
3.
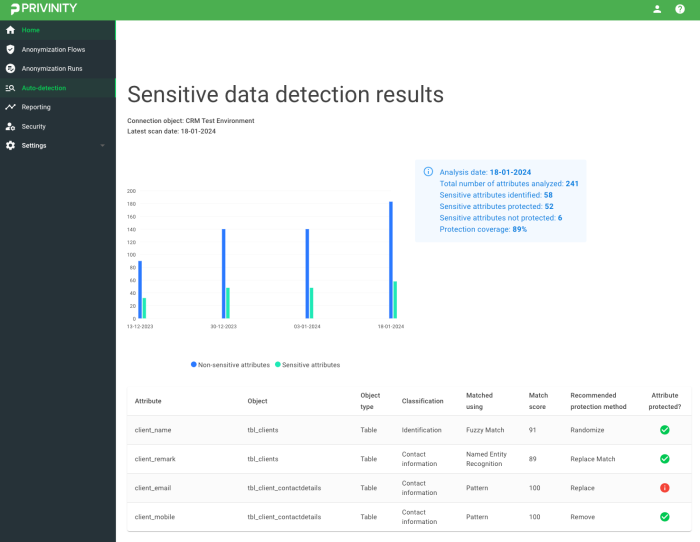
Discover privacy-sensitive data within your data source using our AI algorithms.
Our AI algorithms automatically assess your dataset for privacy-sensitive data and provide recommendations on how to protect it. Even after making new adjustments to your data model, our AI algorithms continue to assist you, ensuring you never overlook privacy-sensitive attributes.
4.
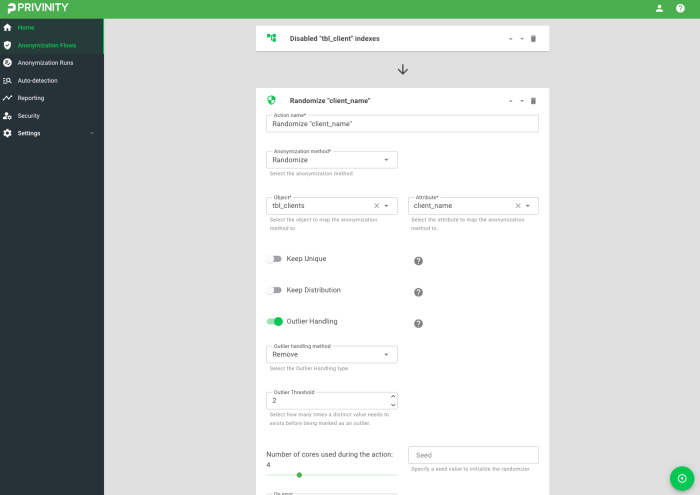
Protect privacy-sensitive attributes the way that fits your use-case
Customize the protection of each privacy-sensitive attribute according to your preferences by choosing from over 10 different anonymization methods. Further personalize your configuration by setting specific options, such as preserving data distributions or conditional anonymization that protects only specific data that meets the condition.
System requirements
Privinity Runtime requirements
Microsoft Windows 10 or Microsoft Windows Server 2016 or higher
4 cores
8 GB RAM
Minimally 15GB of free space

Plan a Proof of Concept
Curious about how the Privinity Privacy Platform can protect the privacy-sensitive data within your organization? Through a Proof of Concept (PoC), we demonstrate all the capabilities within your own environment right away!