Governance
Always in control of sensitive data through your data privacy measures

Thanks to comprehensive logging within the Privinity Privacy Platform, you are fully capable of demonstrating which actions have been performed and by whom. Privinity helps you get and stay in control.
Accessible reporting
The person executing an anonymization configuration is looking for different information than a Chief Information Security Officer (CISO) who wants to know which data is protected. Reports within the Privinity Privacy Platform are tailored to the specific roles of the individuals accessing them.
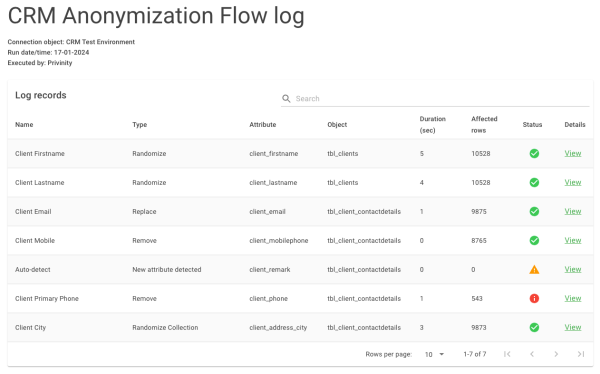
Logging at every level
Every action you perform within your Privinity Privacy Platform environment is recorded. This way, you can always view who executed which action and when.
For example, you can see in detail which attributes within your data sources were anonymized at what time and whether it was successful. You can use this information to demonstrate that you have successfully implemented data privacy protection measures, for purposes such as an audit or the process of becoming a certified organization.
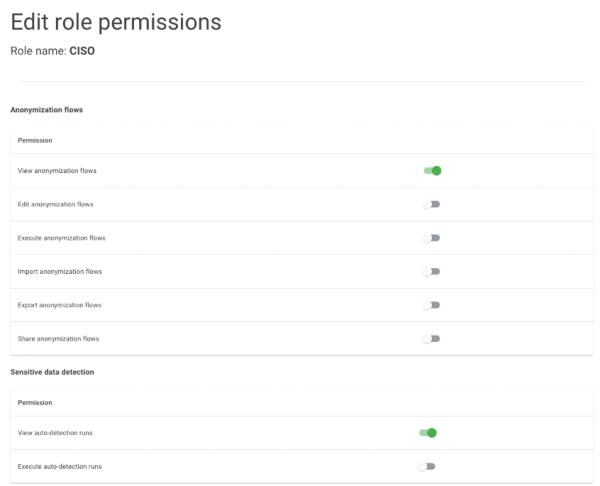
Control at a detailed level who can use which functionality
Within your Privinity Privacy Platform environment, you can determine which role can perform which functionality using our authorization module. This allows you to specify at a detailed level what each role can execute, view, or modify.
In control of the anonymized result
After anonymizing a data source, you naturally want to ensure that it is adequately protected. Therefore, an automatic assessment takes place after anonymization, which checks the entire data source based on various anonymization quality tests, such as k-anonymity.
This information is recorded for each anonymization run, allowing you to easily monitor whether the quality of anonymization increases or decreases as the data in your sources change, through reports and analysis.
Audits and certification
As an organization, you need to demonstrate the measures taken to process sensitive data securely. As a data controller, you are obligated, for example, to comply with GDPR when processing personal data. Similarly, achieving certain certifications may require disclosing the measures in place for secure data processing. With the capabilities of the Privinity Privacy Platform, you are fully equipped to efficiently meet these requirements.


Plan a Proof of Concept
Curious about how the Privinity Privacy Platform can protect the privacy-sensitive data within your organization? Through a Proof of Concept (PoC), we demonstrate all the capabilities within your own environment right away!